My First Experience at BSides SF

Hello Hackers! Today's post is going to be a bit more in the blog style—a reflection on my experience at a local hacker convention. What is B Sides? Why does it exist, why is it called BSides, and what even happens at a hacker convention anyway?
What is BSides?
Well, the story actually starts with a different hacker conference, among the most famous in the world: BlackHat. Started in 1997, "Black Hat has grown from a single annual conference in Las Vegas to a global conference series with annual events in Tokyo, Amsterdam, Las Vegas, and Washington, DC" (taken from Blackhat.com). In 2024 alone, there were over 20,000 participants in the USA, with "more than 100 selected briefings" over the course of the 'Main' Conference. While that might not sound like a particularly high number, when you take into account that the 'Main' Conference takes place over just two days with all levels of specialized cybersecurity training on the other four days, the ratio of content-to-attendees seems a lot more balanced. However, attending this large conference has a price, with the cheapest, early-bird tickets setting you back $2,599*. What happens to cybersecurity enthusiasts who would like the chance to socialize with their peers, listen to talks, attend workshops, get hands-on experience, and network with potential employers, but can't afford the hefty ticket price on top of a flight and hotel to Las Vegas during peak travel season? Some of my readers might be screaming, 'Def Con!' Although DefCon is another, arguably more, renowned hacker convention that also takes place during Summer in Vegas, it too suffers from the same problems stemming from high participation.
Enter BSides. BSides became the alternative event for many presenters who had their talks rejected from being included in the Black Hat program, just because of the high volume of applicants. BSides was started with this problem in mind—even its name (taken from the "B-Side" of a vinyl record) reflects their mission to provide the community with an alternative, approachable, and affordable conference for everyone—students, seasoned professionals, vendors, and everyone in between
If you've been reading this blog post closely, you'll notice that earlier I prefaced this article as being about my experience attending a "local hacker convention," while also mentioning that BSides has its roots in Las Vegas. Without doxing myself, I will make it public that I live in the Bay Area. So how to explain this disparity? Well, while the first BSides did in fact happen in Las Vegas, Nevada, in 2009, it's since grown exponentially due to the community's love of the concept. And who wouldn't love the concept? BSides is an entirely volunteer-run and outsider-friendly conference. To maintain its accessibility and low costs for attendees even in spite of increased popularity, BSides has started sprouting grassroots conferences in major cities around the world—over 50 conferences worldwide, all loosely tied together!
The best part? Every single one is unique, based on the interests of the local community. Every BSides has a local events page where potential participants can submit theme ideas and topics they're interested in learning about. Now, what to expect at a BSides conference? Again, each one is different, but in this post I'll be talking about my first year attending one—more specifically, BSides San Francisco, 2023.
The first step in attending the event was buying a ticket. Although they were extremely well priced at $75 per person for two full days of talks, including buffet-style food and access to the Saturday night party (more on that later), I managed to attend completely free. As a nonprofit and community event, they require a lot of volunteers to actually keep the conference running, which is why they allow volunteers of a certain number of hours entry for free (I don't recall the number specifically, but I believe I worked about 5-6 hours total). For me, trading two volunteer shifts (of a few hours each) for free access to the rest of the program seemed like a no-brainer. Volunteering came with many other benefits, too—networking opportunities with other volunteers, cool volunteer-exclusive shirts, and it also helped me complete some hours for my high school's community service requirement.
When I first walked into the building, I was immediately struck by the scale of the event. The organizers rented out the City View at Metreon, and there were two large floors; the lower floor was part of the 16-screen movie theater housed there (which happens to be home to the second-largest IMAX screen in the USA).

The larger keynotes were held on the bottom floor.

After the opening ceremony, it was straight into the action: as I took the escalator to the second floor along with hundreds of other people, I was overwhelmed with the scene: vendors' booths lining every wall, selling all sorts of security products, busy workshops, demos, and activities. Because of BSide's strict media policy, I can't post any crowd shots, but the top floor was definitely busy.

After walking around for a bit checking out the booths, I started getting hungry. I walked to the food area and was instantly impressed by how delicious the breakfast food was, with plenty of options—a trend that continued through the day.


To this day, the most creative form of advertising I have seen came from the sponsor of the coffee, which was, of course, free to all attendees and served from multiple kiosks all day.

To encourage the less business-oriented participants to interact with the myriad vendors selling products, they implemented a passport raffle system—collect every booth's stamp to be entered in the drawing. Since not everyone wants to spend their time going booth-to-booth, and not everyone who does completes their stamp passport before the midday drawing, the number of participants in the raffle is relatively small—I got lucky and won a book about hacking APIs! Of course, though, I wasn't there for the raffle or the vendor swag (each booth gives out their own free swag); I was there to connect with the community.

The number of individuals I met and connected with in one single day was a record amount—everyone is there to interact in one form or another. I remember seeing a man with dreadlocks, an expensive suit, and a sleek watch next to a girl with bright pink hair, a skull-and-bones T-shirt, and fingerless gloves—an outfit that walked straight out of a hacker movie. Any conference that can bring together such a wide spectrum of people is doing something right, especially since IT and the tech industry in general often suffers from a lack of diversity.

Anyways, besides the talks from local talent, which are all available on YouTube if you're curious: BSidesSF 2023 - Opening Remarks - Day 1: Reed Loden, there's a lot of other things to keep yourself busy with. For example, there's the badge challenge- this year it was an astronaut badge.

'Badgelife', as it's been coined, is the hacker culture that arises from the custom, artistic circuit boards handed out to select participants at some cybersecurity conferences. What started out as a way to prevent ticket counterfeiting has now evolved into legendary challenges—oftentimes the badges hold elaborate puzzles that participants can try to solve. DEFCON (another conference mentioned earlier) started this tradition, with some of the badge challenges requiring multiple days to solve, including using other people's badges—the press badges, the vendor badges, the presenter badge, etc. While I cannot personally write about these crazy challenges, I can highly recommend listening to the Darknet Diaries podcast, episode 43, for a crazy story about how the host, Jack Rhysider, acquired the famous and highly coveted Black Badge from DEFCON. The black badge is the highest honor a DEFCON Attendee can receive (and DEFCON is the largest hacking convention in the world). If you're interested in cybersecurity in general, his podcast is the best out there, and he also posts his transcripts online, so you can read through them like an article (check out darknetdiaries.com/imgs/black-badge-contest.pdf for a taste of what the challenges entail). Although BSides SF's 2023 badge challenge is not quite as intricate, it depicted an astronaut with hidden LED's that would light up when you solved each stage in the challenge. Although I got stuck on the fourth level and eventually moved on since there was a lot to see, some people were walking around with badges that had all six areas lit up.
Additionally, in a lot of cybersecurity conferences, there's the concept of a "village"—a physical area within the event where a certain area of specialization meets. For example, at DefCon, there's a car hacking village where people can watch and learn how to hack cars. There's also a satellite hacking village (and yes, at last year's DefCon there was a targetable Space Force satellite, "Moonlighter," in low orbit as part of the competition to hack into it). Many fields of cybersecurity are represented more in depth at these villages. At BSides, there was sadly no satellite hacking, but there was an internet-of-things (IOT) village where I learned how to remotely turn off a smart light bulb by running some configuration commands and a Python script. While I want to learn more about how the exploit worked, it was more of a demo to show the potential flaws within these devices. If I had stuck around for longer, I probably would have learned more (especially since there were a couple of guys who were trying their luck at hacking a smart TV and getting a walkthrough from the village experts), but there was a lot to do, so I moved on. The next village I visited was devoted to physical security—AKA Lockpicking Village. By far one of the most crowded villages, locking picking holds a special place with hackers; it's a physical representation of what we do online. To quote one of my favorite TV shows, Mr. Robot:
"The lock pick. Every hacker's favorite sport. The perfect system to crack, mostly because unlike virtual systems, when you break it, you can feel it. You can see it. You can hear it." (S1.Ep2).
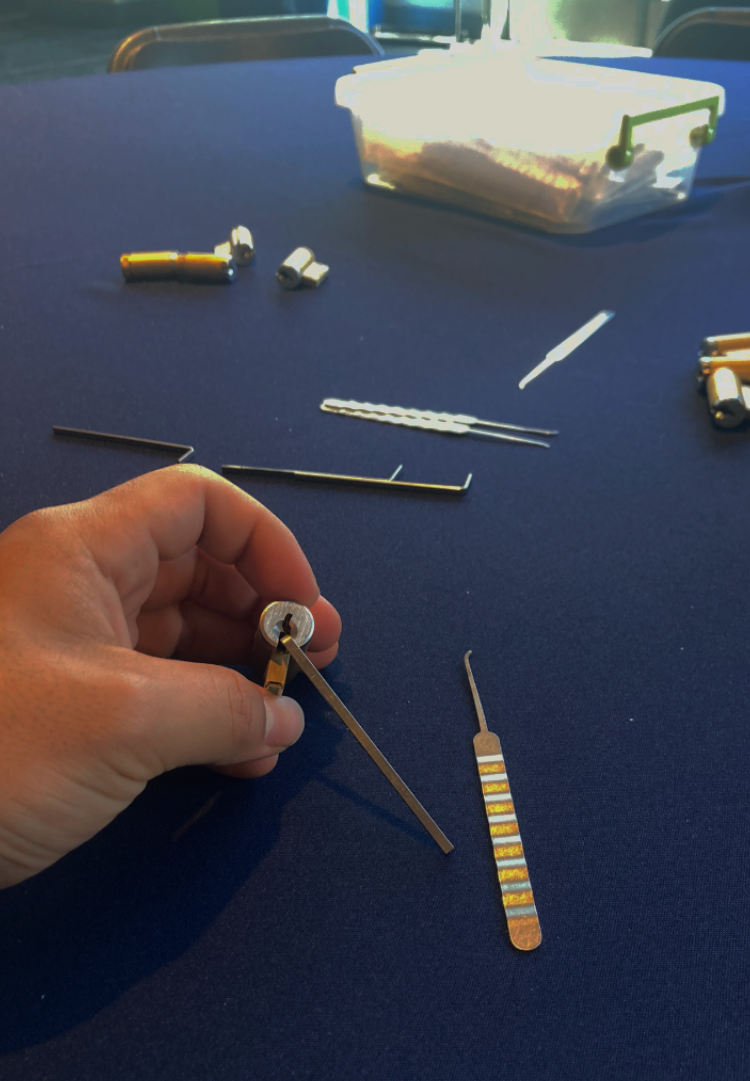
At this table, there was this friendly guy named Rick, who helped me build my confidence with picking locks. They had a range of difficulty, from one pin (some small file cabinets only have one pin) all the way up to six (most traditional door knobs have five or six). The more pins, the harder it gets, as you have to line up each pin to a certain height and keep it there (this is called the shear line, and it's why keys have little teeth that push each pin in the lock up to a certain height to enable the cylinder to turn). This post is by no means a lockpicking tutorial, as I'm not an expert, and I should also note that picking locks that you are unauthorized to open is illegal. At lockpicking village, they had all the tools, including tension bars and shims, rakes, and a variety of picks. They even had transparent locks, which helped visualize how locks work. If you're at all interested in how to lockpick, I highly recommend trying, as it can be a useful skill to have, even if you don't think you'll often use it. For example, once at a sports practice, I was able to unlock an equipment bin for my team that my assistant coach didn't have the key to because I had a lockpick set in my backpack (shoutout to Rick). Again though, that was done with permission, and I would recommend against picking locks you're unauthorized to pick.
After walking around the villages, I followed a sign and ducked into this backroom, which was surprisingly large. It seemed like a large conference room with a lot of tables set up, with power strips placed on the tables, and people glued to their computers, laser-focused on their screens.

On the whiteboard, there was a leaderboard projected. I found an empty spot at a table and immediately connected to the Capture-the-Flag (CTF) platform. The concept of a CTF is to find vulnerabilities intentionally placed by the moderators—these are the 'flags'. Once you exploit a vulnerability, you're presented with a flag you can only find by hacking, which you then verify on the CTF platform for points—the harder the challenge, the more points you receive. They're usually presented in a jeopardy style, with different categories of specialization: open-source intelligence (OSINT), networking, cryptography, web application exploitation, log analysis, password cracking, enumeration, scanning, and more. This was not my first CTF, but this one definitely felt like it had higher stakes, as everyone in the room was working through the challenges and the energy was very high. Also, besides the categories mentioned earlier, the BSides CTF had an in-person challenge—a lock hooked up to a circuit board encased in a small wooden tower—all hooked up to a receipt printer that would provide you the flag if you successfully picked the lock.
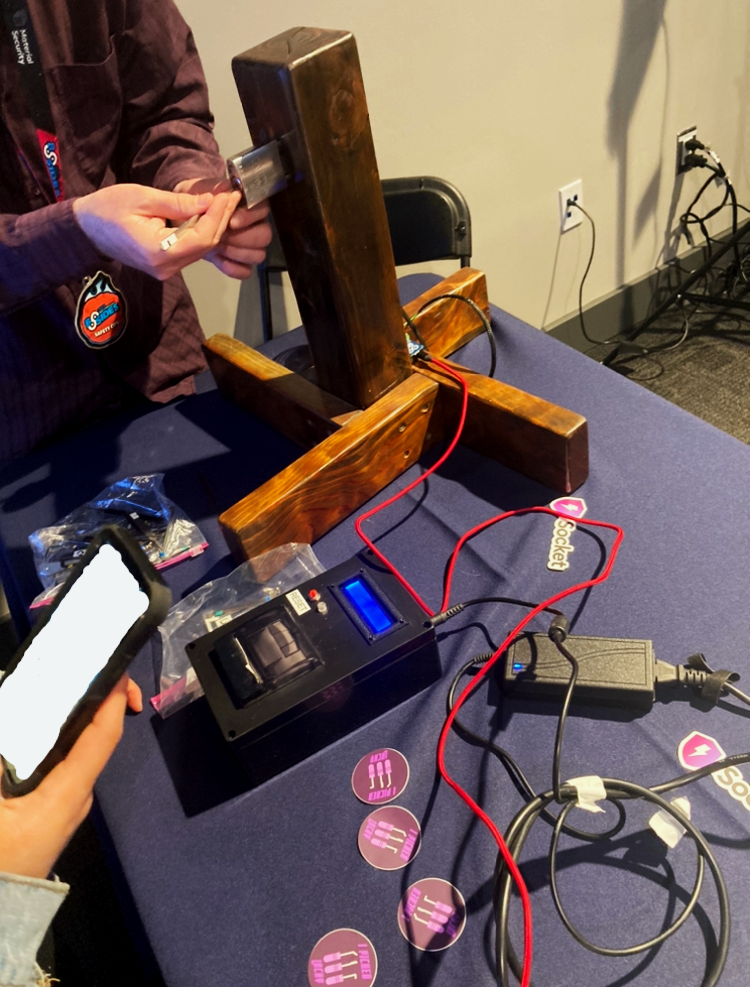
Although everyone else seemed to be much more knowledgeable, it was still very fun, and at the end of the day, when the CTF was over, I didn't come in last on the leaderboard. Plus, I got some amusing memories out of it—like the printed 'flag' receipt, which still lives in my room to this day.
The whole BSides event was incredible, but the party on Saturday night was really one of the most memorable experiences. There were the staple party ingredients—food, drinks, music, dancing—but there were also pinball machines, retro arcade games, glow in the dark stars, and a lot of astronaut-themed decor. The organizers even hired entertainers—dance crew @oaklandoriginalz—who put on quite the break dancing show—all while wearing space suit costumes. For their grand finale, they lined up four members from the audience, in order from shortest to tallest, and had them bend over at the waist. Then, the lead dancer got a running start and not only cleared them but did a backflip over them! Although everyone was taking videos, because it has stills of the crowd, I cannot post it, so you'll just have to take my word for it.
In conclusion, BSides SF was an incredible experience and helped me to learn and grow as a student of cybersecurity in more ways than I expected. You make good connections, learn new skills, and get a view into just how broad cybersecurity-related things can be. I would highly recommend anyone interested in checking out cybersecurity conferences to look up their local BSides and attend, or if there isn't one in your city, start one! </>
*Price in USD, for attending Black Hat USA 2024 in person (including all in-person briefings), taken from the Black Hat Registration page (https://www.blackhat.com/us-24/registration.html).
References
- BSides San Francisco — Official Website: https://bsidessf.org/
- BSidesSF Talks Playlist — YouTube: https://www.youtube.com/playlist?list=PLbZzXF2qC3RuQAuC0C4Q7Lk4eQluqIVzL
- BSides Conference Series Overview — InfoSec Conferences: https://infosec-conferences.com/hub/event-series/bsides/
- A History of "Badgelife" — DEF CON's Artistic Circuit Boards (VICE): https://www.vice.com/en/article/a-history-of-badgelife-def-cons-unlikely-obsession-with-artistic-circuit-boards/
- How DEF CON Hackers Got Involved with the Space Force (Politico): https://www.politico.com/news/2023/08/11/def-con-hackers-space-force-00110919
- The Coveted DEF CON Black Badge — Adobe Developer Blog: https://blog.developer.adobe.com/the-coveted-defcon-black-badge-7e5952c0d1bb